Secure Your HTTP/2 Infrastructure Against Rapid Reset Attacks
Realistic Threat Simulation
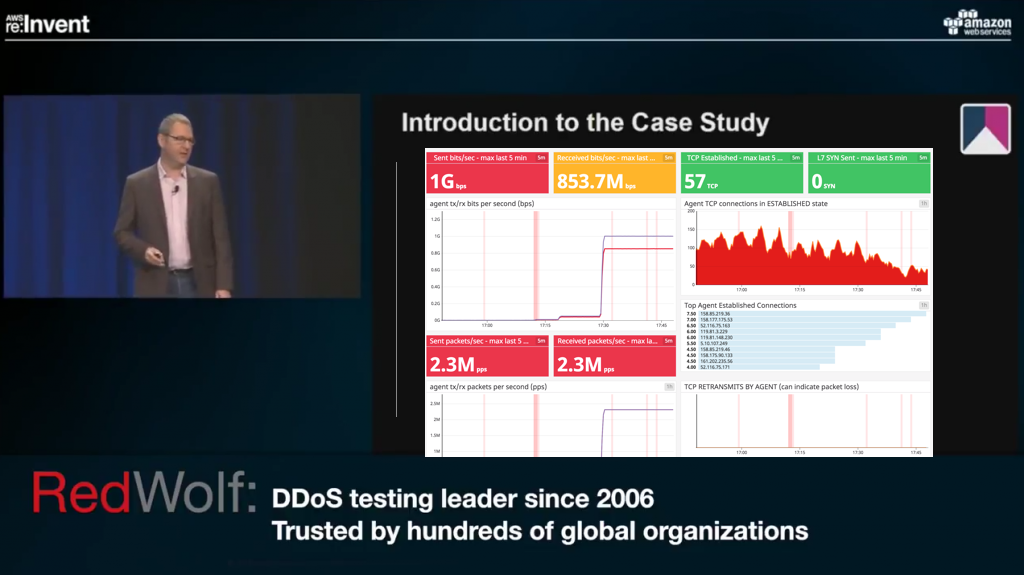
Improving SOC Capability Since 2006
The most comprehensive, safe, and feature rich threat simulation platform available for enterprise.

External Threat Simulation
DDoS, Load Tests & More

Internal Threat Simulation
Data Leaks, Malware/APT, Policy Abuses

Situational Awareness
Monitoring, Data Fusion

Next Generation SOC
Supercharge your security operations teams
RedWolf is famous for Cloud & DDoS Testing
RedWolf's next-generation platform is trusted by hundreds of Fortune 2000 companies. With it you can safely validate your defense performance, improve alerting and detection, calibrate mitigation systems, optimize operational responses and confirm SLAs and controls.
Trusted Vendor
#1 provider of Threat Simulation for Fortune 500 companies since 2006!
Class Leading Capabilities:
Outage free testing: Precision real-time control & feedback systems.
DDoS testing: Over 300 DDoS scenarios: TCP, UDP, ICMP attacks, IPV4/6, HTTP, DNS, SSDP, SMTP, NTP, IPSEC, GRE & many many more Load testing: Real users, API testing, mobile-apps.
Device testing: Targeted: Firewalls, WAF's, IPS, Load Balancers, DNS Servers, and more Build repeatable test-library. Full API for automation.
Benefits
Get the most from your defense and monitoring systems (ROI) Rapidly improve defense posture Faster incident response & mean time to resolution.
Comprehensive Insider Threat
RedWolf's next-generation platform is trusted by hundreds of Fortune 2000 companies. With it you can safely validate your defense performance, improve alerting and detection, calibrate mitigation systems, optimize operational responses and confirm SLAs and controls.
Most Attack Vectors & Scenarios
Over 200 internal threat scenarios: Data Leaks/DLP, Gaming, Chat, Content, Insecure Protocols, Malware, Advanced Persistent Threats & many many more!
Scenarios cover over 90% of all Insider Threat cases.
Automation
API allows easy integration & scheduled testing.
Leverage RedWolf sensor fusion to correlate scenario against SIEM evidence.
Enabling rapid problem identification
The era of the 'Dashboard' is coming to an end. Today's security operations teams have too many dashboards, too many systems, too many services, too many events. RedWolf has turned this inside-out and created an intelligent command and control panel.
Beyond just Dashboards
Too much adaptive visualization prioritizes useful information.
Anomaly detection.
Automated assessment.
Command and control.
Information Sources
Monitoring: Netflow, Packets, Web, DNS, TCP, ICMP, SMTP, SNMP, Traceroute, BGP, and more.
Events & Alerts: SIEM (Splunk, ELK, ArcSight, ...), Syslog, Host-based-agents
Device API's Cloud Providers, Routers, Firewalls, DDoS Devices, Load Balancers, any REST API
Integrate disparate systems
Integrations: Over 400
Cloud? YES
Local? YES
Agentless? YES
Agent Based? YES
Next Generation SOC
Formally Model Operations & Technologies
Visually manage your KPI's, incident response procedures, runbooks and align them to the technology and data.
Expert-Guided Option
RedWolf can analyze your servers and build a world-class reusable test library.
Content
Runbooks, training, catalogs, use-cases.
Hundreds of Fortune 2000 companies trust RedWolf

























"Security Control Testing with RedWolf Security provides us with the assurance that our technology, controls and operations work effectively.”
We have been using RedWolf Security since 2016, and I have to say they have transformed the way we approach our mandatory security control testing. Testing with RedWolf Security provides us with the assurance that our technology, controls and operations continue to work effectively. Redwolf has enabled us with an effective and economical way to validate our investment in defense infrastructure.
As risk to infrastructure increases exponentially, we are confident RedWolf will continue to exceed our expectations. RedWolf’s easy-to-use platform and flexible API enable us to validate and improve our security posture year over year.
RedWolf Security remains the vendor of choice for security control testing initiatives.
"Security Control Testing with RedWolf Security provides us with the assurance that our technology, controls and operations work effectively.”
We have been using RedWolf Security since 2016, and I have to say they have transformed the way we approach our mandatory security control testing. Testing with RedWolf Security provides us with the assurance that our technology, controls and operations continue to work effectively. Redwolf has enabled us with an effective and economical way to validate our investment in defense infrastructure.
As risk to infrastructure increases exponentially, we are confident RedWolf will continue to exceed our expectations. RedWolf’s easy-to-use platform and flexible API enable us to validate and improve our security posture year over year.
RedWolf Security remains the vendor of choice for security control testing initiatives.
Crownpeak, Amazon Web Services (AWS)
One Million HTTPS Requests/sec? No problem! RedWolf Hardens Cloud Infrastructure to Record Levels!