August 15, 2017
What attack vectors do you support?
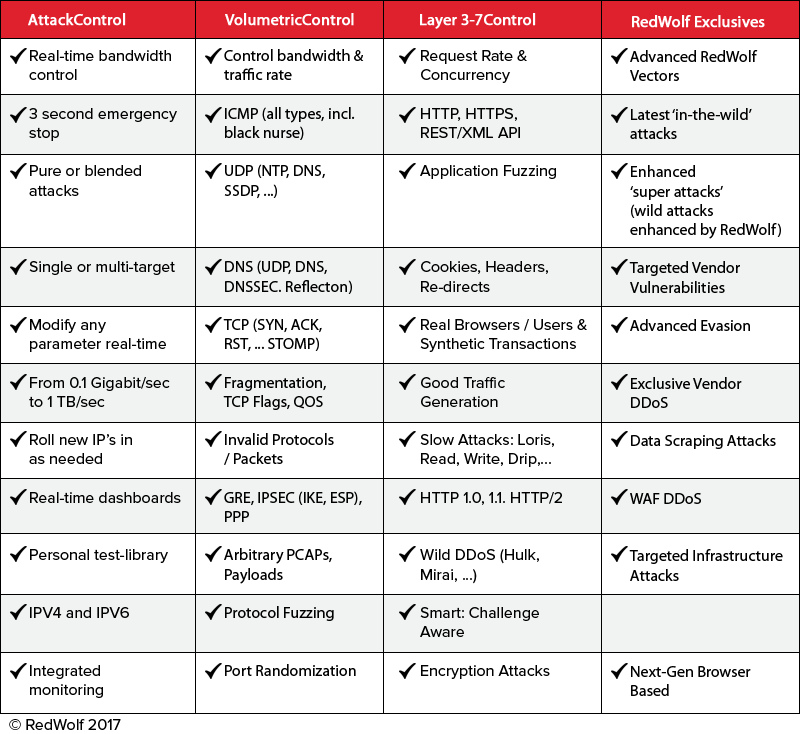
As of 2017 RedWolf’s attack vector library has over 300 different vectors. Most vectors have numerous parameters that can be tweaked/customized. An NDA is required to see the full list as it is a closely held secret.
What’s more important than the list of attack vectors is the control over them — this is where RedWolf leads the industry. RedWolf can:
- Stop traffic in 3 seconds — fastest in industry.
- Control exactly where the traffic comes from by provider, region, or even an individual IP.
- Control traffic precisely with smooth ramp-up/down of bandwidth, connections, requests.
- Make live changes to any parameter in real-time — excellent to test adaptive defenses.
- Create complex ramp-up’s, attack-groups, blended-attacks, multi-target attacks.
- And more
Here is a summary of the platform’s technical capabilities: