September 13, 2017
What kind of targets and attack vectors should I try?
What you should try first depends on your network environment and the kinds of assets you are protecting. We recommend going through an exercise to map your environment and identify your targets.
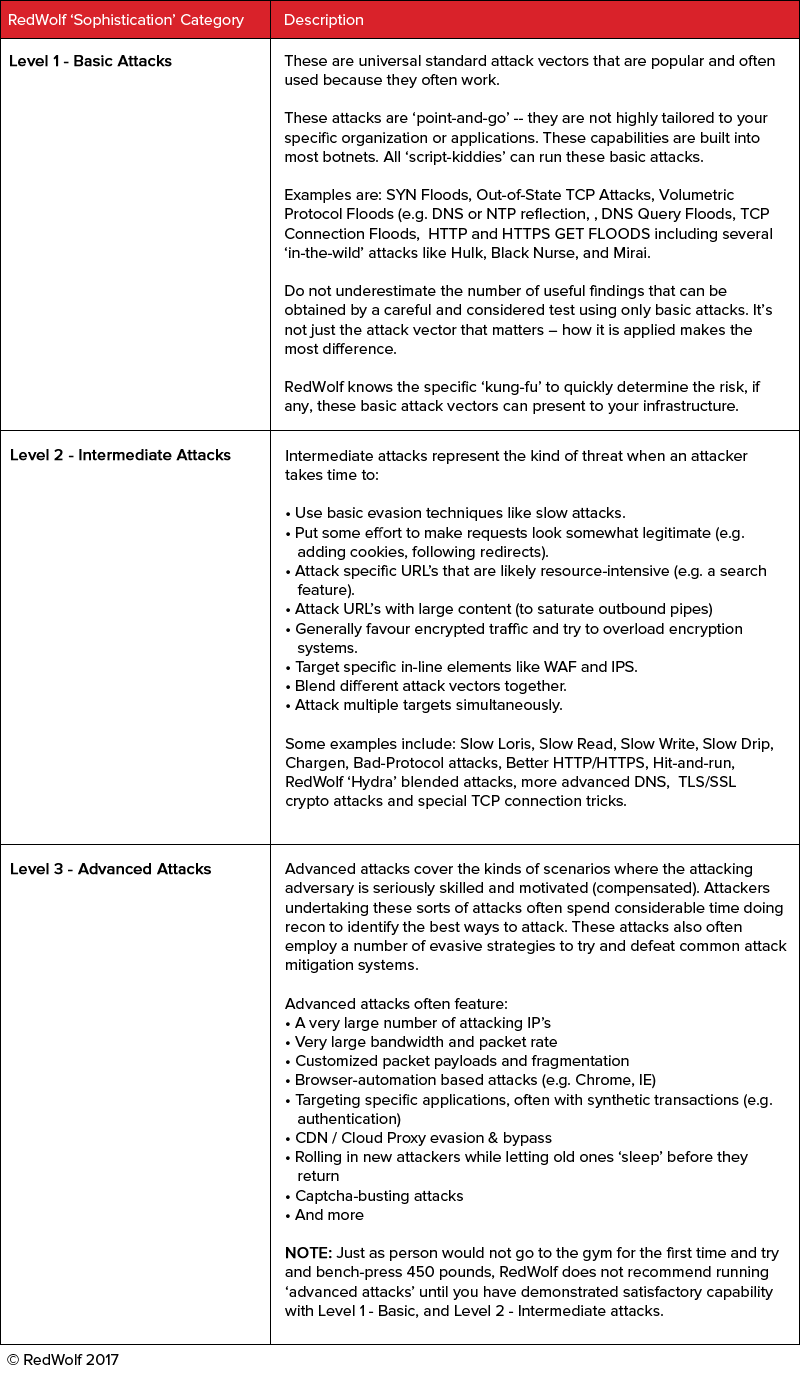
RedWolf offers customers a spreadsheet based test scoping template. Using this template will help narrow down the kinds of vectors that can be run. Remember that RedWolf has over 300 attack vectors as well as ‘kung-fu’ on how they are deployed vs. defense systems. The possibilities can be overwhelming so to help we’ve grouped the attack vectors & strategies into escalating levels of complexity as follows:
In a perfect world, the best way (i.e. the highest value outcome) involves running three tests, each with different focus:In a perfect world, the best way (i.e. the highest value outcome) involves running three tests, each with different focus:
Test 1: Baselining
• Determines the 50% and 70% performance/CPU thresholds of the critical services.
• Recommend testing up to 10 targets. Recommend local DNS, HTTP and HTTPS services,
• This is not an ‘attack’ but a ‘load test’. It identifies key performance thresholds that can be back-propagated to defense systems.
• If you do not know what throughput your services can give, how can you protect them?
• This should be run:
• At least once per year on all critical Internet facing services
• After every significant network change (to ensure that controls have been re-established properly)
• For each new deployment of an Internet-facing service
Test 2: Local Mitigation
• Tests local infrastructure, attack mitigation, load-balancers, and services under controlled attack conditions.
• Targets that should be included include the previous targets as well as VPN’s, communications services (e.g. Mail (SMTP & Web Mail access), and conferencing (e.g. Skype for Business)).
• Test first with 80% “Level 1 – Basic”, and 20% “Level 2 – Intermediate attack vectors”. Only after these are all ranked ‘Good’ or better should “Level 3 – Advanced” attack vectors be considered.
• Most vectors ramp-up carefully and slowly to identify any vulnerabilities before defenses activate.
• RedWolf tests a number of aspects on the local environment:
• Impact to user experience during test
• Infrastructure performance: routers, firewalls, load balancers, DNS and Web servers, during ramp-up
• Attack detection speed and accuracy
• Performance & utilization monitoring systems
• Mitigation control effectiveness
• Leakage & corresponding impact
• False positive detection
• Operational awareness / root-cause identification & control over systems
• This should be run as follows:
• Every year: repeating previous year’s weakest tests, adding in new targets and increasing the attack sophistication.
• followed by re-tests to ensure that any deficiencies have been addressed and that test coverage has been given to all critical targets
Test 3: 3rd Party / ISP / Cloud Mitigation
• Trusting a 3rd party with the fate of your organization shouldn’t be based on ‘blind-faith’, it should be ‘demonstrated capability’.
• RedWolf tests a number of aspects of cloud DDoS mitigation services:
• Impact to user experience during test
• Activation procedure (if not always-on)
• Specific cloud defense controls / mitigation approaches
• Quality of monitoring / alerts / notifications / communications / portal
• Speed of attack detection and mitigation
• Time to mitigate completely
• Leakage & corresponding impact
• False positive detection
• Adaptability to changing attack vectors
• Ideally this should be run with a 4-6 hour test window PER 3rd party defense system. In a 4 hour test window up to 8 different attack scenarios can be tested. This will include volumetric, connection-oriented, various Layer 7 attacks.
• This should be run:
• At least once a year for a ‘main-test’ of each 3rd party mitigator
• Followed by a re-tests to ensure that any deficiencies have been addressed and that test coverage has been given to all critical targets.
• Once for every new service protected by the 3rd party.
