Understanding and Running “Middlebox TCP Reflected Amplification Attacks” with the RedWolf Platform
January 18, 2023
Middlebox TCP-reflected amplified attacks are a new DDoS attack vector, first disclosed in August 2021 by researchers from the University of Maryland and the University of Colorado. These attacks were first observed in the wild in 2022. This novel attack vector enables highly amplified TCP traffic, which was previously impossible, and allows for amplification rates surpassing those of common UDP reflection vectors.
What are “Reflection Amplification Attacks”?
Reflection attacks involve an attacker spoofing a victim’s IP address and sending a crafted request to a server, causing the server to respond with a larger payload to the spoofed address. This allows attackers to “amplify” the attack by only having to send small payloads while having the servers send high amounts of traffic to the victim. In the past, these attacks were typically carried out using UDP-based protocols due to the 3-way handshake of TCP complicating spoofing attacks, as without receiving the SYN/ACK, the attacker can’t make valid requests “from” the victim.
What makes this different than UDP amplification attacks?
TCP-reflected amplification attacks exploit middleboxes that are deployed in a non-TCP-compliant way by responding to out-of-state packets and applying content restriction policies. Attackers take advantage of this by sending an out-of-state spoofed source IP packet containing host headers with a blocked site. The middlebox responds with HTTP headers or HTML pages, which are much larger than the original packet, providing significant amplification. This occurs despite the connection being incomplete due to the middlebox being configured to assume that it may have missed some packets.
Previously, SYN attacks required a 1:1 ratio of bandwidth from the attacker to the victim. However, by exploiting non-compliant middleboxes, attackers can amplify their attacks by as much as 75:1. Middleboxes with certain configurations can also cause a self-perpetuating infinite loop by resending the previous packet every time the victim responds with an RST packet, effectively creating an infinite amplification potential for attackers.
How to Simulate a TCP reflection Attack from the RedWolf Portal
In addition to existing UDP amplification attacks, RedWolf Security has added three new TCP Middlebox Amplification Attacks that can be run from the RedWolf Portal:
- TCP HTTP Middlebox
- TCP HTTPS Middlebox
- TCP DNS Middlebox
When running TCP Reflection attacks, RedWolf Agents act as middlebox servers (though they are not actually vulnerable) and send amplified traffic to your targets, allowing you to test your infrastructure against this emerging threat.
With the RedWolf portal, you can adjust the attack traffic in real-time to test your DDoS scrubbing systems and pinpoint the precise moment when defenses activate and start scrubbing. The ability to blend multiple attack vectors simultaneously also allows you to test your systems against advanced and harder-to-defend attacks.
To test your systems against TCP Middlebox Reflection Attacks, simply select one (or more) of the Middlebox attack vectors in the scenario designer, choose the traffic generators, and select which targets will receive the middlebox traffic.
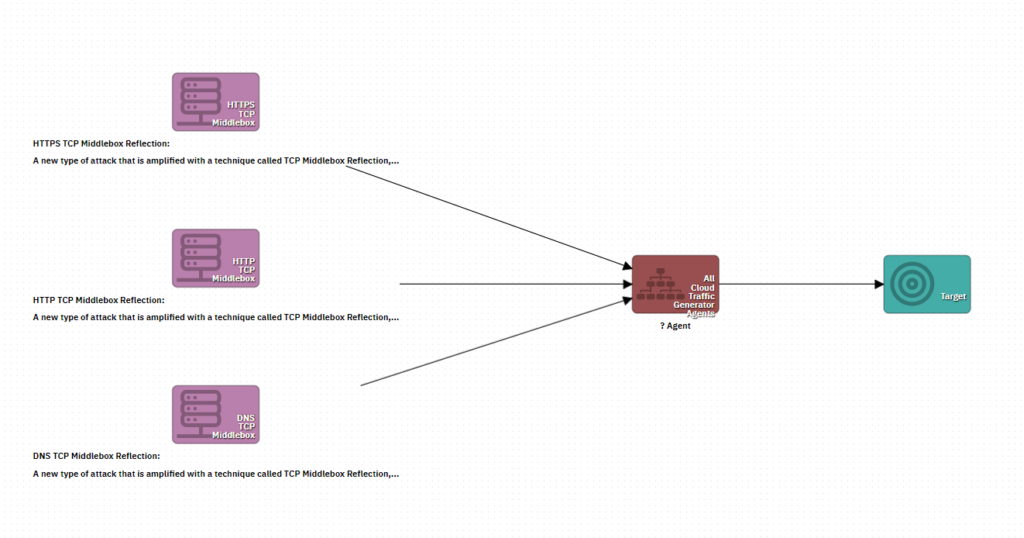
Creating a blended TCP Middlebox attack using all three new TCP Middlebox Attack Vectors in the RedWolf scenario designer.
Additional Resources:
https://www.akamai.com/blog/security/tcp-middlebox-reflection
https://www.youtube.com/watch?v=OSfgTbjb3og
https://geneva.cs.umd.edu/posts/usenix21-weaponizing-censors/
https://geneva.cs.umd.edu/papers/usenix-weaponizing-ddos.pdf
