RedWolf Technical Details
August 15, 2017
Q: Can a Virtual Machine be provided to be used as a target for the testing?
YES. RedWolf offers a downloadable VMware virtual machine ‘agent’ that can be used in local networks (typically labs) to generate traffic. Even though these agents are local they are still controlled from the same ‘control.redwolfsecurity.com’ portal.
The amount of traffic a local VM can generate is limited by the VM hardware itself. With a 10 Gigabit/sec NIC on typical hardware a local traffic generator can generate reliably over 9 Gigabit/sec with jumbo frames and about 5 Gigabit/sec with small 1500 byte frames without much optimization. Some clients have achieved higher with 40 Gigabit/sec NIC’s but these systems required optimizations.
A single VM can generate thousands of HTTP and HTTPS requests/sec.
Multiple VM’s can be ‘ganged together’ as required.
Individual teams can use their own VM’s – that is, multiple users can use different internal VM’s in their tests. They do not need to ‘act in unison’ and can be individually addressed.
Instrumented versions of the followings services are available:
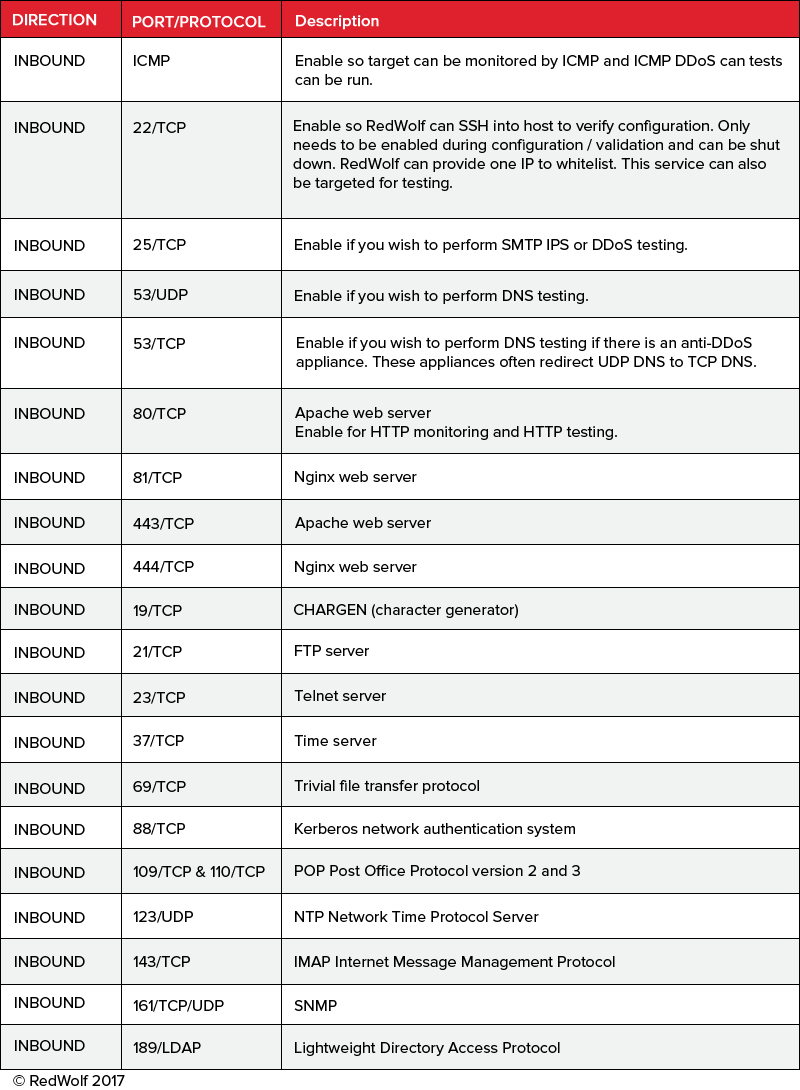
Note, the test target can be positioned at different levels with the network being tested.
Suggestions are:
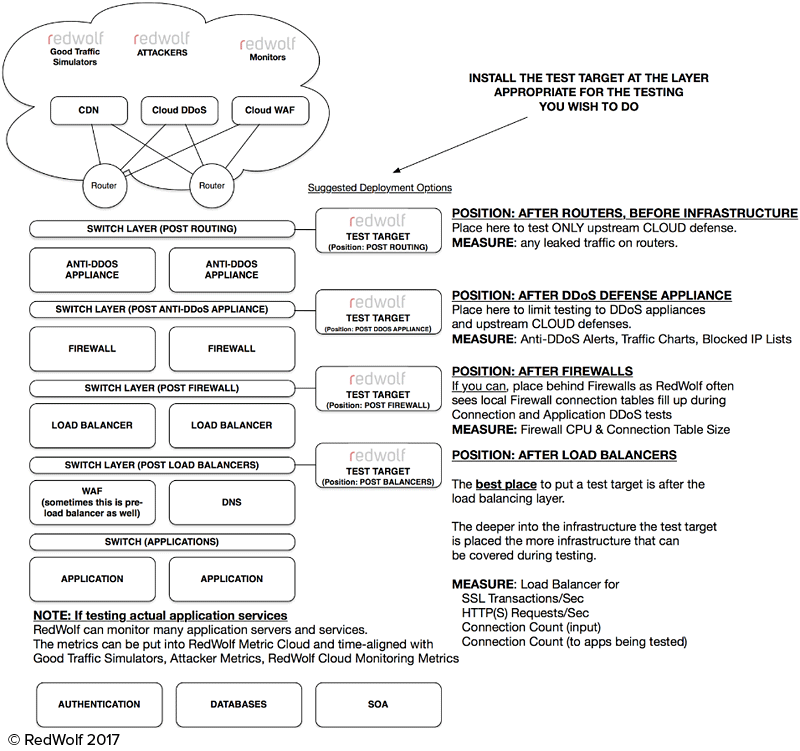
Q: What attack vectors do you support?
As of 2017 RedWolf’s attack vector library has over 300 different vectors. Most vectors have numerous parameters that can be tweaked/customized. An NDA is required to see the full list as it is a closely held secret.
What’s more important than the list of attack vectors is the control over them — this is where RedWolf leads the industry. RedWolf can:
- Stop traffic in 3 seconds — fastest in industry.
- Control exactly where the traffic comes from by provider, region, or even an individual IP.
- Control traffic precisely with smooth ramp-up/down of bandwidth, connections, requests.
- Make live changes to any parameter in real-time — excellent to test adaptive defenses.
- Create complex ramp-up’s, attack-groups, blended-attacks, multi-target attacks.
- And more
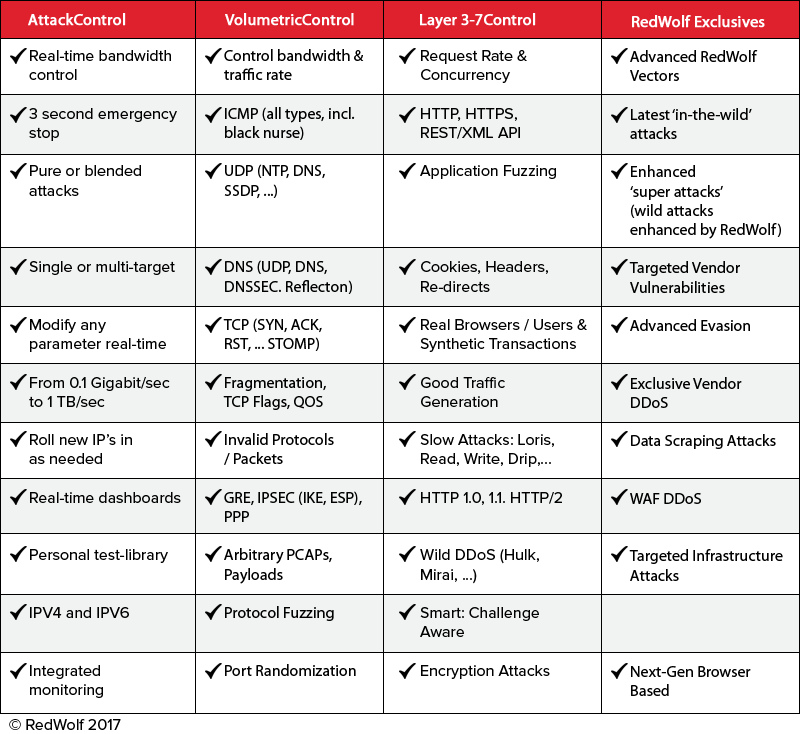
Here is a summary of the platform’s technical capabilities:
Q: Do you have the ability to customize request headers and cookies?
YES RedWolf can customize all HTTP headers and randomize any parameter of them.
MANY PARAMETERS AVAILABLE: In addition to headers, protocol options like HTTP 1.0, 1.1, /2, keep-alive on/off, cache control, cookies can also be supplied and randomization options.
These are all available to users to edit in the visual test designer in the portal.
RECOMMEND RATE-CONTROLLED (1/s) PRE-TEST QA:
When complex headers and cookies are set up for some requests RedWolf recommends running very low level (a single IP, 1-2 request/sec) against a target to verify that the parameters are working as expected. Modern applications sometimes set a large number of headers with unusual values and it is a good idea to test these requests to ensure the load balancer and application logic will respond as expected to the requests. Because RedWolf has the ability to traffic-limit the HTTP(s) request rate this is easy to do and recommended prior to doing a ‘big test’.
Q: Do you have the ability to send traffic based on IP rather than URL?
YES all attacks can target an IP vs. a domain name. For protocols like HTTP the correct host name (or names) can be supplied for the test. This allows testing of ‘vips’ and segregated load balancer configurations or individual name servers.
NOT ONLY BY IP vs DNS BUT ALSO ASN:
RedWolf can put agents in many places and can perform a traceroute from the agents to the target and source traffic from agents that traverses a specific network path or ASN. This can often be done without having to resort to any BGP work.
Q: Some attack countermeasures need to be reactive. Please describe how testing scenarios account for the implementation of reactive controls
THE ART OF THE RAMP-UP of traffic from very low levels is a very popular and sensible way to test. As traffic is increased it places increased load on many network devices and servers. At some point a ‘weak link’ in the chain will start expressing high-enough stress that the team will want mitigation to activate.
HOLD LEVELS STEADY RedWolf can hold traffic steady at that level while reactive measures are put in place.
LOW AND SLOW attacks are the most common ‘reactive’ types of attacks where default mitigation settings have to be adjusted but most Layer 7 attacks can involve some art in reactive control management.
GOAL: PERFECT THRESHOLDS – One of the goals RedWolf helps clients achieve is when a mitigation threshold activates smoothly before a protected server goes down.
GOAL: MASTERS OF DEFENSE – Once the operationalization of threshold changes is old-hat RedWolf can change the mode to be more ‘wargame’ like with more dramatic changes in parameters beyond traffic levels. It takes time to develop these operational skills and the only way they can be developed is with live exercises like RedWolf offers.
